Windows Sleek Performance is the latest FakeVIMES family dangerous rogue antispyware. It generates fake security \ virus detection popups and alerts, blocks Windows explorer and redirects Google search links.
Where the popups are shown, it is likely to be combined with Blue Screen of Death. The original Screen is shown by Windows when it is out of order and critical error needs to be fixed. The one which is meant there is certainly a fake. It is popped up for the same purpose as the fake warning.
Adware simulates a reboot and shows a string of popups eventually drawing users to its FAKE activation page.
To get rid of Windows Sleek Performance and similar misleading softwares, click here to run free scan.
Where the popups are shown, it is likely to be combined with Blue Screen of Death. The original Screen is shown by Windows when it is out of order and critical error needs to be fixed. The one which is meant there is certainly a fake. It is popped up for the same purpose as the fake warning.
Adware simulates a reboot and shows a string of popups eventually drawing users to its FAKE activation page.
To get rid of Windows Sleek Performance and similar misleading softwares, click here to run free scan.
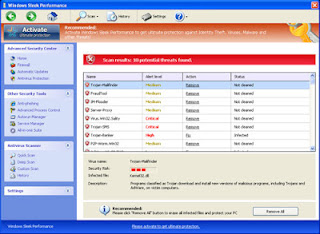
Windows Sleek Performance snapshots:
Windows Sleek Performance activation code (helps removal):
0W000-000B0-00T00-E0020
NOTE: "Activating" Windows Sleek Performance
is not enough. You need to remove related trojans \ rootkits using
reliable malware removal solution.
It is important to fix Windows registry after Windows Sleek Performance malware removal using safe registry cleaner software.
Windows Sleek Performance manual removal guide:
Delete infected files:
%AppData%\NPSWF32.dll
%AppData%\Protector-[random 3 characters].exe
%AppData%\Protector-[random 4 characters].exe
%AppData%\W34r34mt5h21ef.dat
%AppData%\result.db
%CommonStartMenu%\Programs\Windows Safety Checkpoint.lnk
%Desktop%\Windows Safety Checkpoint.lnk
Delete Windows Sleek Performance registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “WarnOnHTTPSToHTTPRedirect” = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegedit” = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegistryTools” = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableTaskMgr” = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorAdmin” = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorUser” = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “EnableLUA” = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Inspector”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “net” = “2012-4-27_2″
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “UID” = “tovvhgxtud”
HKEY_CURRENT_USER\Software\ASProtect
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\[random].exe

No comments:
Post a Comment