Windows Active Defender is a new shift in counterfeiting as this time the black hats have applied advanced rootkit techniques. Rootkits are used to create special environment, with the main goal to restrict user’s and security programs in the their access to the components within the special environment.
Naturally, this trick seriously aggravates removal of Windows Active Defender. Besides, the part of memory that hides the counterfeited program might also include other threats.
Being more secured against extermination attempt than its counterparts in faking the malware produces its silly popups with stunning and increasing frequency. If you fail to get rid of Windows Active Defender at the early day, preferable starting the process right now, you might be too late as the adware, if not killed, starts killing computer system. After certain point, the process becomes irreversible.
Naturally, this trick seriously aggravates removal of Windows Active Defender. Besides, the part of memory that hides the counterfeited program might also include other threats.
Being more secured against extermination attempt than its counterparts in faking the malware produces its silly popups with stunning and increasing frequency. If you fail to get rid of Windows Active Defender at the early day, preferable starting the process right now, you might be too late as the adware, if not killed, starts killing computer system. After certain point, the process becomes irreversible.
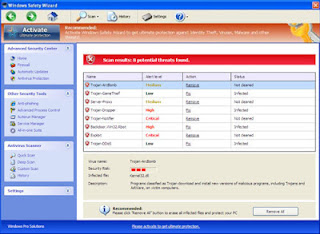
Windows Active Defender screenshots:
Windows Active Defender activation code (helps removal):
0W000-000B0-00T00-E0020
NOTE: "Activating" Windows Active Defender
is not enough. You need to remove related trojans \ rootkits using
reliable malware removal solution.
It is important to fix Windows registry after Windows Active Defender malware removal using safe registry cleaner software.
Delete infected files:
%AppData%\NPSWF32.dll
%AppData%\Protector-[random 3 characters].exe
%AppData%\Protector-[random 4 characters].exe
%AppData%\W34r34mt5h21ef.dat
%AppData%\result.db
%CommonStartMenu%\Programs\Windows Active Defender.lnk
%Desktop%\Windows Active Defender.lnk
Delete Windows Active Defender registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “WarnOnHTTPSToHTTPRedirect” = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegedit” = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegistryTools” = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableTaskMgr” = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorAdmin” = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorUser” = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “EnableLUA” = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Inspector”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “net” = “2012-4-27_2″
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “UID” = “tovvhgxtud”
HKEY_CURRENT_USER\Software\ASProtect
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\[random].exe

No comments:
Post a Comment