The pretended tool for computer security turns the situation upside down. While viruses are free to multiply, download other viruses, if system security settings so provide, the fake security tool does not remain idle too. It detects the most frequently used files and states that these are viruses. Basically, in some cases it might chance to be true and the situation is quite understandable, for the files that belong to virus body are usually used frequently as many of viruses are self-launchers, which means they start their files by their own and at least once per Windows session, normally at the very beginning of it.
Nevertheless, most of the files specified by the counterfeits are names of pretty harmless, and what is important to take into account, useful files. If you delete them, you put useful software and computer system at risk of malfunctioning and collapse, as well as there is a risk of deleting in such a way a piece of precious data.
Remove Windows Work Checker and please consider its scan results as intentional false positives aimed at tricking users. Click here to get a free scanner installed on you PC to guarantee extermination of the adware and real viruses.
Nevertheless, most of the files specified by the counterfeits are names of pretty harmless, and what is important to take into account, useful files. If you delete them, you put useful software and computer system at risk of malfunctioning and collapse, as well as there is a risk of deleting in such a way a piece of precious data.
Remove Windows Work Checker and please consider its scan results as intentional false positives aimed at tricking users. Click here to get a free scanner installed on you PC to guarantee extermination of the adware and real viruses.
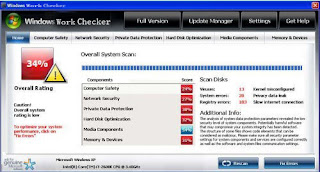
Windows Work Checker interface snapshot:
Windows Work Checker remover download:
Windows Work Checker manual removal info:
Delete infected files:
%UserProfile%\Application Data\Microsoft\.exe
Delete infected registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\afwserv.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR " = '1'

No comments:
Post a Comment