Windows Test Master is a content detected to be a carriage for a host of trojans and a content spammed though instant messenger services and bot spam centers. Perhaps, distributors of the software also try to spread its copies by direct introduction from infected website through the vulnerabilities of software active on the targeted computer system while the system is being connected to the aggressive website.
The program is also readily available for download from its web-pages. Visitors to those pages are collected from hijacked web-browsers and from other websites, which, whether deliberately or due to oversight, allowed publishing advertisement link for such a tricky software.
Get rid of Windows Test Master regardless of the way the adware has been injected. It pretends to conquer viruses, but, as matter of fact, it could be defined as a virus itself.
While the pretended security tool is pretending to safeguard computer systems, any real security guard cannot properly run. In the other words, security mechanisms of computer system infected with the above malware are completely disabled. Hence it is and easy prey for program-predators that abound in the worldwide web and local networks.
To remove Windows Test Master and other malicious residents of your computer system in one move, click here to start free scan and ensure detections and disposal of malicious residents of your PC (or quarantining for dubious infections).
The program is also readily available for download from its web-pages. Visitors to those pages are collected from hijacked web-browsers and from other websites, which, whether deliberately or due to oversight, allowed publishing advertisement link for such a tricky software.
Get rid of Windows Test Master regardless of the way the adware has been injected. It pretends to conquer viruses, but, as matter of fact, it could be defined as a virus itself.
While the pretended security tool is pretending to safeguard computer systems, any real security guard cannot properly run. In the other words, security mechanisms of computer system infected with the above malware are completely disabled. Hence it is and easy prey for program-predators that abound in the worldwide web and local networks.
To remove Windows Test Master and other malicious residents of your computer system in one move, click here to start free scan and ensure detections and disposal of malicious residents of your PC (or quarantining for dubious infections).
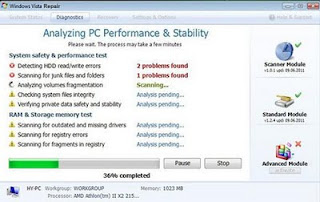
Windows Test Master snapshot:
Manual removal guide:
Delete Windows Test Master files:
%UserProfile%\Application Data\Microsoft\.exe
Delete infected registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\afwserv.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR " = '1'